Array
(
[1536x1536] => Array
(
[width] => 1536
[height] => 1536
[crop] =>
)
[2048x2048] => Array
(
[width] => 2048
[height] => 2048
[crop] =>
)
[rta_thumb_no_cropped_420x] => Array
(
[width] => 420
[height] => 0
[crop] =>
)
[et-pb-gallery-module-image-portrait] => Array
(
[width] => 400
[height] => 300
[crop] => 1
)
[et-pb-post-main-image-fullwidth-large] => Array
(
[width] => 0
[height] => 0
[crop] => 1
)
[et-pb-image--responsive--desktop] => Array
(
[width] => 1280
[height] => 720
[crop] => 1
)
[et-pb-image--responsive--tablet] => Array
(
[width] => 980
[height] => 551
[crop] => 1
)
[et-pb-image--responsive--phone] => Array
(
[width] => 480
[height] => 270
[crop] => 1
)
)

Carl FransenMy passion is to make my mark on the world in a positive and lasting way. I want to set an example for my son that his father can compete with integrity in today’s world, be very successful, and leave the world a better place for him. Combining my...
Discover More
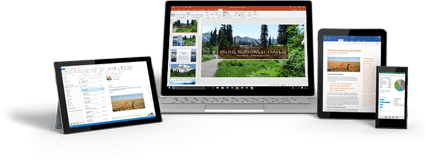
Thinking of Switching Your Email to Office 365,But Not Sure Which Plan Is Right? Look no further for information. Office 365 is built for your business. The tools included with Microsoft’s service allows businesses to work better together no matter where users are...
Discover More

GIBON is a new type of ransomware that first emerged on the scene last week and has since been utilized in a wide range of cyber-attacks. The main way this GIBON-variant is spread is by malspam with an attached malicious document, which contain macros that will...
Discover More

Most business owners are aware that not all IT companies are equal. They also know that not all subscribers get equal service guarantees or packages – even though you may pay the same price for them. With CTECH Consulting Group, however, you get an all-inclusive array...
Discover More

Over the last few decades, technology has helped business owners of all kinds make giant strides. Whether it’s better serving clients, optimizing internal processes or driving increased profit margins, there’s no denying technology has played a key role in the...
Discover More
Page 2,681 of 2,814« First«...102030...2,6792,6802,6812,6822,683...2,6902,7002,710...»Last »






